4 Of The Most Common Encryption Methods

Trustless, borderless, immutable. Cryptocurrency as we know it wouldn't exist without cryptography. And one of its use cases is blockchain encryption methods.
Deciding on one is the first step to achieving the three most important goals in crypto: security, decentralization, and scalability of the blockchain trilemma. So far, there's no absolute solution that gets all three right. Which is why there are so many blockchains, each with different encryption methods.
While they might sound abstract and technical, we use them all the time with crypto wallets and payments.
Quick Takes
- Encryption is the application of cryptography that protects blockchain data from other users.
- Cryptography involves both encryption and decryption (such as wallet private keys). Encryption doesn't necessarily enable decryption, which makes immutability possible (e.g., for transaction blocks).
- Common encryption methods are AES, RSA, Triple DES, and ECDSA/EdDSA.
- Cryptography is an obfuscation method. Other common related methods include hashing, ZK-proofs, stealth addresses, ring signatures, and mixnets.
Cryptography 101: What Is Encryption?
Encryption refers to computing methods that transform plain text into unreadable content or ciphertext. This "cipher" consists of a message, a code word (or key), and a pattern. This pattern can be as complex as letter-position swaps, math equations, or substitution tables. The goal is to send the message from party A to B without revealing it to other parties.
It might sound simple because you only need to share the key with both users. That's what's called symmetric encryption. It's a key shared with every user you want to get the message.
The problem is: the more people have this key, the easier it is for the wrong person to find it. It's the opposite of decentralization:
- Decentralized means that you can't control a system from a single entity. You need to control at least half of all "nodes" (users, devices, keys...)
- Symmetric encryption means that, because all use the same key, one compromised node is enough to compromise everything.
Imagine you share a Metamask wallet with nine trusted people, so you all use the same private key/seed phrase. Even if you all use it responsibly, there's ten times more risk that someone outside the group finds it. Either by accident, fraud, or blockchain's lack of privacy.
If you know the key, you can decrypt or revert the cipher.
To prevent this, there's a second type: asymmetric encryption. It uses a complex math function to generate two linked keys. It's slower than the alternative, and the logic behind it is beyond the scope of this post. (But you can check this video for a simple analogy)
It looks like this:
Message + Key1 = Ciphertext
Ciphertext + Key2 = Message
Where Key1 is shared and Key2 is secret.
And it basically means:
- There's a public key that you share when sending the message and a private key you keep secret.
- The message recipient also has a public key to respond and a private key to decrypt your message.
- If you receive a message, you just need their public key and your private key to decipher it. If you send a message, the recipient needs your public key but not your private one.
- You cannot decipher messages only knowing both private keys (unless you spend ridiculous time and computer power on trial and error).
Similarly in crypto, you can see anyone's wallet and transactions. But you can't access or use those funds without the private key. It's as secure as your ability to keep your key unknown.
Top 4 Most Used Encryption Methods
Symmetric or asymmetric, every encryption method falls into one of those categories. The latter is the most common in crypto, although symmetrical encryption is also used depending on the purpose. Here are the best four with examples:
1. RSA
RSA is an asymmetric encryption method invented by three MIT computer scientists: Ronald Rivest, Adi, Shamir, and Leonard Adleman. It's based on complex mathematics and while secure, it's slower than other methods. In a nutshell, it works like this:
- Suppose you want to send a message from User A to B, but an omnipresent User C can see all data sent in between. The goal is to keep the information confidential between A and B.
- The RSA algorithm generates a public and private key for each. User A can share its public key and also see B's public key. Neither of them ever knows nor shares each other's private keys.
- According to RSA, it's easy to multiply but hard to factorize large numbers. This creates a one-way equation that's very difficult to revert. Thus, users can derive public keys from private ones without being reverted to private keys.
- First, the receiver user B generates his keys and shares the public one. User A uses User B's public key to encrypt his message. After sending it, User B will use the private key to decrypt User A's message.
- User C can steal the ciphertext and public key. But because they don't have private ones, it's unreadable.
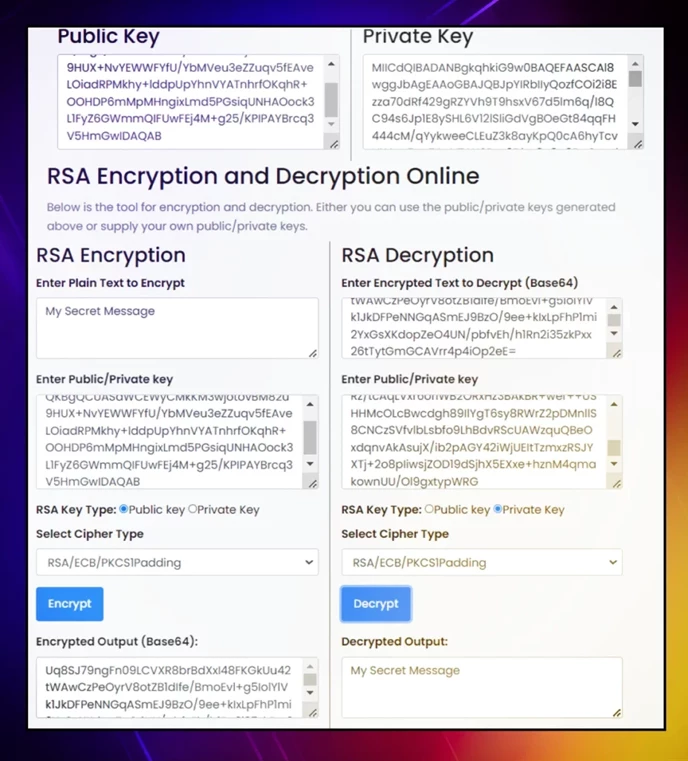
In asymmetric encryption, using the same public key to revert ciphertext results in decryption failure. You can try it yourself with this online RSA encryption tool:
RSA is used as the foundation of ECDSA, which is an improved and lighter version used for cryptocurrencies. Although a few use the original RSA (e.g., Hedera Hashgraph, HBAR), it helps understand the next method:
2. ECDSA
The Elliptic Curve Digital Signature Algorithm (ECDSA) uses different math for the RSA logic. The function is harder to revert than RSA's factorization, and the values draw an elliptic curve when expressed on the charts (hence the name). While more difficult, Elliptic Curve Cryptography (ECC) is a simpler equation, so you can achieve the same security with shorter keys.
ECDSA has the right balance of security and encryption speed. It's why it's used by Bitcoin, Ethereum, Ripple, Litecoin, BNB Coin, Cosmos, and a dozen others. Others like Cardano, Monero, and Polkadot use the faster EdDSA variant (Edwards-curve Digital Signature Algorithm).
3. Triple DES
Triple DES (3DES) leverages one of the first-ever encryption methods: the 1970s Data Encryption Standard. It's the symmetrical encryption of a 64-bit key and was widely used until cracked in 1997. Instead of one-way functions, it's a text conversion to 64-bit blocks and bit permutation. A bit like swapping alphabet letters.
Triple DES uses the same standard, except it applies three times using a different key each time. This new DES exponentially increased cracking difficulty, but it also tripled the encryption time. While many tech companies have used it, 3DES was cracked in 2016 before most cryptocurrencies appeared.
A faster alternative to 3DES was AES.
4. AES
The Advanced Encryption Standard hasn't been cracked yet, as it's exponentially safer than the other two.
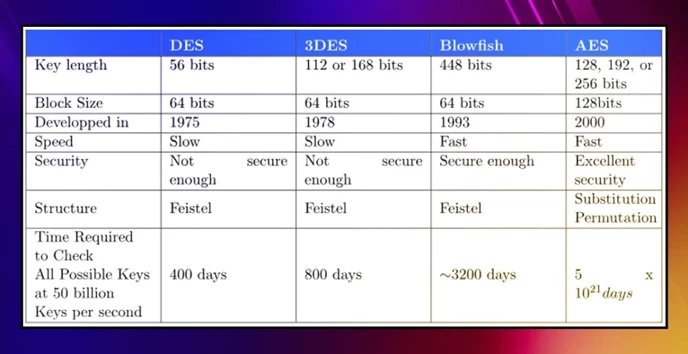
It's different from DES in that it uses 128-bit blocks instead of 64 (even 256), and instead of "Feistel Networks," it uses SPN (Substitution Permutation Networks). It's the standard used on Bitcoin Core to encrypt validator wallets (where the password is the decryption key).
AES is broadly used outside cryptos, such as in the NSA or the browser's HTTP protocol. If you want to see what it looks like, click on the padlock next to the search bar, then "Connection Is Secure," and "Certificate is valid." Browser's AES uses two keys called "SHA-256 and SHA-1 fingerprints."
Common Encryption Alternatives in Crypto
Encryption is just one part of cryptography, which is one of the many obfuscation techniques. To encrypt is to make information unreadable. To obfuscate is to make the meaning or information intent confusing or incoherent.
Blockchains use different obfuscation methods that can't be classified as encryption but fulfill similar goals. Here are some of them:
ZK Proofs
Zero-Knowledge proofs are essential in Ethereum to remain efficient while decentralized. Given a problem or puzzle, ZK-proofs allows one user to verify that they know the solution, without revealing it to the user verifying it. This helps protect sensitive information like passwords, identities, or financial information.
For example, computers "know" when you entered the wrong or right password, even though the servers don't store any. That's because computers convert your input with a one-way function (irreversible) into asymmetric ciphertext. This cipher preserves the same patterns from the original information, which means that by comparing both, you're going to find the same relationships.
Here's a detailed analogy of how ZK Proof works.
Hashing
Encryption is a two-way method, either by using the same key or a private one. Hashing is a one-way method that takes block information and converts it to a fixed string of numbers and letters. Entering the same data generates the same hash, but reverting a hash to the same data requires years of trial and error. Arguably impossible.
No matter the algorithm, every coin with a blockchain uses hashing. Bitcoin's is called SHA-256 and is a more complex version of this:
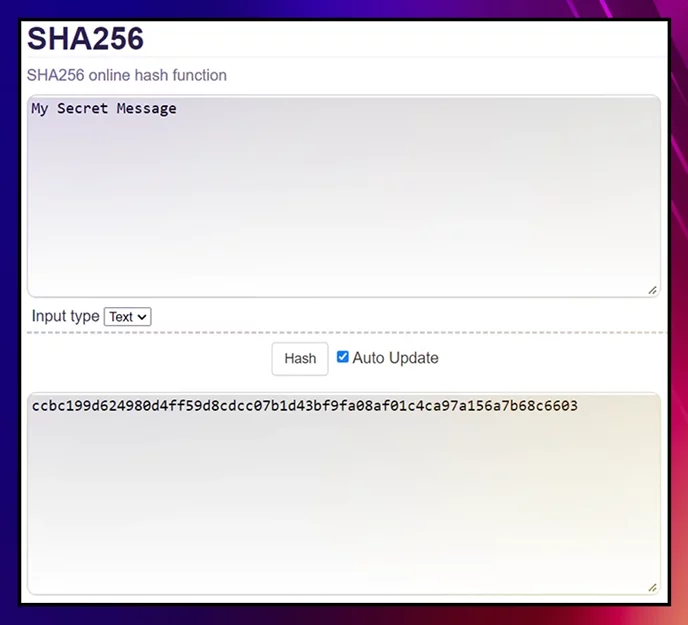
If we add just one space at the end of the message, it's a completely different string:
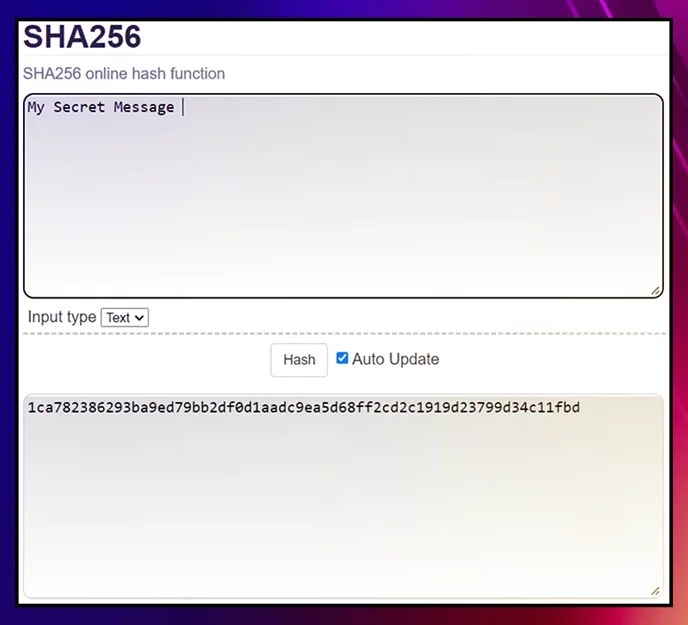
In order to add a new block to a cryptocurrency chain, this data block has to include the hash of the previous block.
Is Encryption Enough To Secure Blockchain?
It's hard to imagine a secure blockchain that doesn't use some encryption method. They're essential for secure decentralization, just as it is for Internet browsing. But it's not infallible.
Security in crypto involves more challenges beyond protecting information. Maybe one day, quantum computers will be able to crack most encryption methods within seconds. Maybe they don't scale well, or they're too slow or expensive to be used.
EdDSA and ECDSA have worked wonderfully across different blockchains. But other problems threaten security such as centralization, faulty consensus models, and code vulnerabilities. With cryptocurrencies, security and decentralization go hand in hand. That's why networks like Ethereum and its forks (Pulsechain) — while not the fastest — tend to be the most secure.
Join The Leading Crypto Channel
JOINDisclaimer:Please note that nothing on this website constitutes financial advice. Whilst every effort has been made to ensure that the information provided on this website is accurate, individuals must not rely on this information to make a financial or investment decision. Before making any decision, we strongly recommend you consult a qualified professional who should take into account your specific investment objectives, financial situation and individual needs.

Max
Max is a European based crypto specialist, marketer, and all-around writer. He brings an original and practical approach for timeless blockchain knowledge such as: in-depth guides on crypto 101, blockchain analysis, dApp reviews, and DeFi risk management. Max also wrote for news outlets, saas entrepreneurs, crypto exchanges, fintech B2B agencies, Metaverse game studios, trading coaches, and Web3 leaders like Enjin.

Development
Knowledge
Subscribe To Newsletter
Stay up-to-date with all the latest news about
Liquid Loans, Fetch Oracle and more.
Copyright © 2024 Crave Management.
All Rights Reserved.

The LL Librarian
Your Genius Liquid Loans Knowledge Assistant